We have seen how to implement K8s Gateway API and access the services that are in the same cloud network, using the Gateway and HTTPRoute resources.
Now, what if a service is in a different cloud environment and you have to access it from the Gateway i.e., multicluster, multicloud scenario? I’ll walk you through a demo here and show you how to set up a multicluster, multicloud Gateway with Kubernetes Gateway API.
Multicluster Kubernetes Gateway demo overview
We have two clusters: one in EKS (primary) and the other in GKE (remote). I have deployed Istio in both the clusters and the setup is primary-remote Istio installation. Istio is used as the controller to implement the Gateway API resources.
Here’s what I’m going to do:
- In the primary cluster/EKS, deploy the helloworld-v1 deployment, helloworld service, and echoserver service.
- In the remote cluster/GKE, deploy helloworld-v2 deployment, helloworld service, echoserver deployment, and echoserver service.
- Deploy the Kubernetes Gateway API resources — Gateway and HTTPRoutes — in the primary cluster.
- After the deployments, we will verify that the Gateway in the primary cluster/EKS can access the services in the remote cluster/GKE, as shown in the image below:
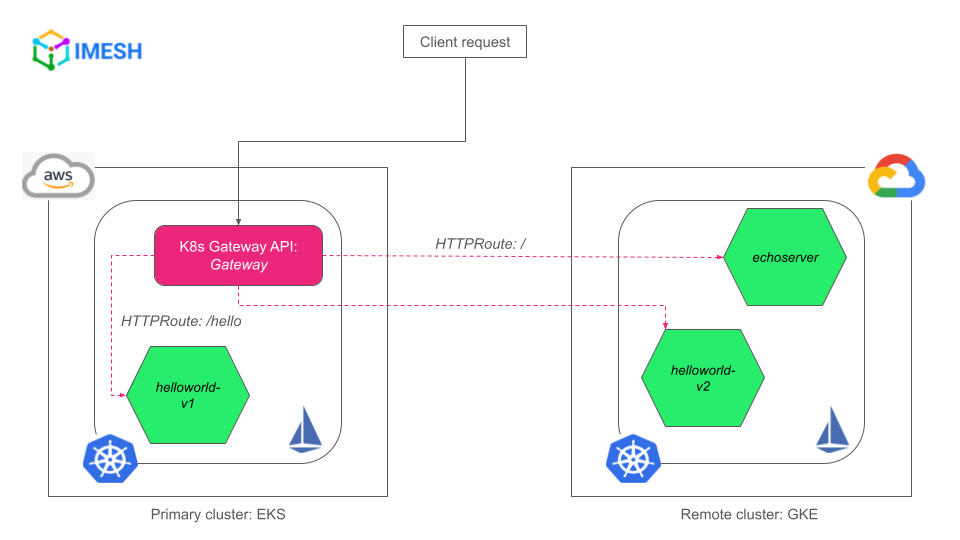
Multicluster, multicloud Gateway with K8s Gateway API demo setup
Deploy the applications and services in clusters
Deploying helloworld-service in both the primary and remote clusters:
kubectl -f apply helloworld-service.yaml --context=eks-cluster
kubectl -f apply helloworld-service.yaml --context=gke-clusterDeploying helloworld-deployment-v1 to the primary cluster/EKS and helloworld-deployment-v2 to the remote cluster/GKE:
kubectl -f apply helloworld-deployment-v1.yaml --context=eks-cluster
kubectl -f apply helloworld-deployment-v2.yaml --context=gke-clusterDeploying echoserver-service in both the clusters and echoserver-deployment only in the remote cluster:
kubectl -f apply echoserver-service.yaml --context=eks-cluster
kubectl -f apply echoserver-service.yaml --context=gke-cluster
kubectl -f apply echoserver-deployment.yaml --context=gke-clusterNote that service resources need to be deployed in both clusters for this to work. That is why I deployed the echoserver-service in the primary cluster/EKS although the deployment is only in the remote cluster/GKE.
Now, let us verify the deployments in both the primary and secondary clusters:
kubectl get svc -n demo --context=eks-cluster
kubectl get pods -n demo --context=eks-cluster
kubectl get svc -n demo --context=gke-cluster
kubectl get pods -n demo --context=gke-cluster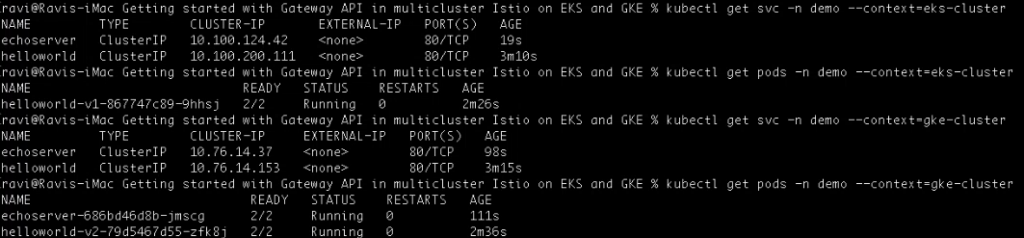
The primary cluster has the helloworld-v1 pod running, while the remote cluster has both helloworld-v2 and echoserver pods running successfully:
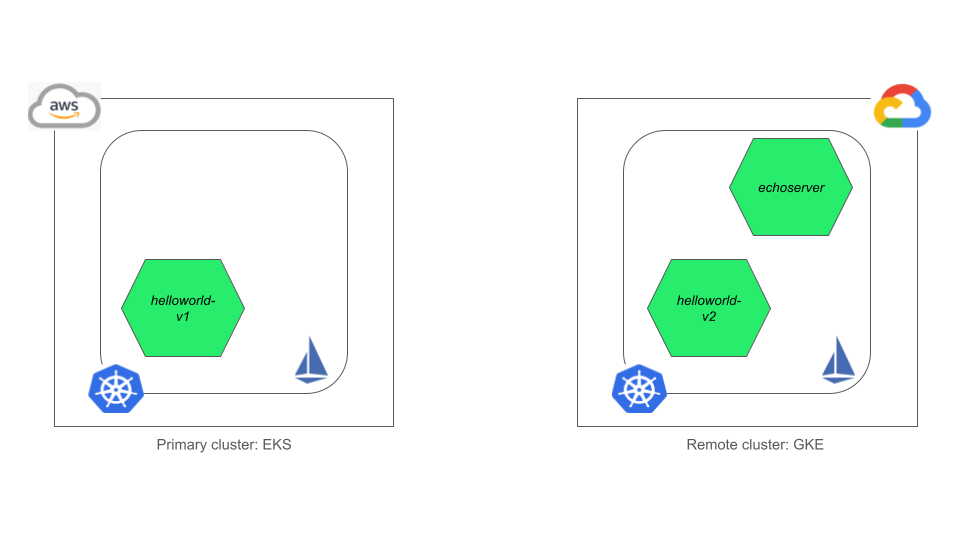
Deploy K8s Gateway API resources and verify multicluster communication
Applying the gateway resource in the primary/EKS cluster:
kubectl apply -f gateway-api-gateway.yaml --context=eks-clusterThe Gateway uses Istio as the controller and is deployed in the istio-ingress namespace.
Deploying HTTPRoute in the primary cluster for helloworld application, which listens on path /hello:
kubectl apply -f helloworld-httproute.yaml --context=eks-clusterNow, let us verify multicluster communication by curling helloworld application, but first, we need to get the Gateway IP:
kubectl get svc -n istio-ingress --context=eks-clusterVerifying multicluster communication:
curl your_gateway_external_ip/hello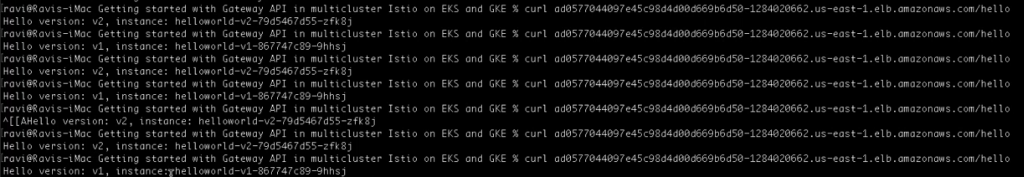
You can see that the request is served by both the helloworld-v1 and helloworld-v2 that are deployed in the primary and secondary clusters, respectively.
Now, let us deploy the HTTPRoute for echoserver in the primary cluster, which listens on / :
kubectl apply -f echoserver-httproute.yaml --context=eks-clusterVerifying if the Gateway is able to access echoserver deployed in the remote cluster:
curl your_gateway_external_ip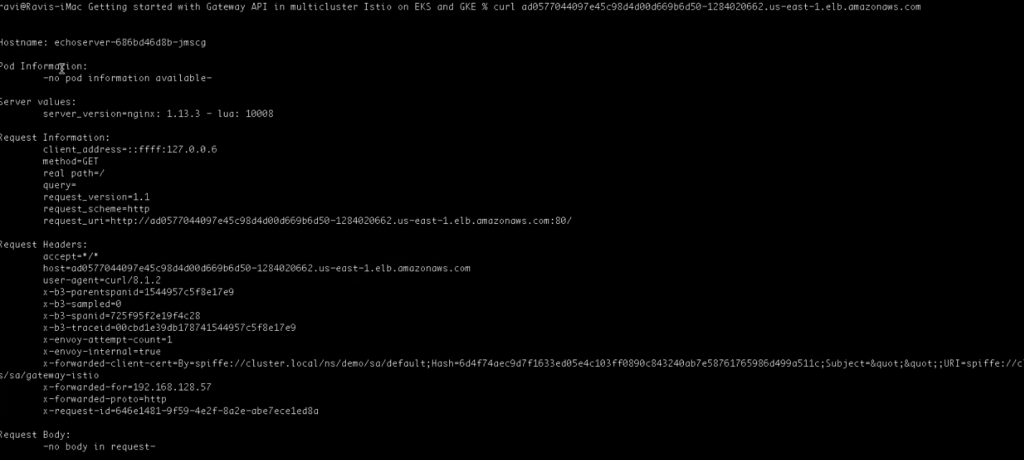
The Gateway is able to get response from echoserver deployed in the remote cluster successfully. And that is the end of the demo.
Securing traffic in Gateway API
Check out the blog, TLS with Kubernetes Gateway API, to see a demo on securing traffic in Gateway API. It shows how to set up 2 listeners (HTTP & HTTPS) at the Gateway and attach HTTPRoutes to them to enable TLS.
If you need help with configuring multicluster or multicloud communication with Gateway API, feel free to reach out to us.






