After supporting multiple clients in the US and India in adopting OSS Istio and Envoy Gateway, we realized that our clients struggle with adopting Cilium. Now that Isovalent is part of Cisco, there is a common concern among adopters about the potential for vendor lock-in. Secondly, we have first-hand experience with how Cilium and Istio service mesh can sometimes conflict in the cluster and result in a performance downgrade.
After all that story, we’ve added Cilium CNI to our enterprise support portfolio. (Please note, our support is restricted to Cilium CNI only and not towards Cilium mesh.)
Suppose you’re evaluating Cilium, migrating from Calico/AWS CNI, or already running it in production. In that case, IMESH provides 24×7 support, SLAs, design reviews, performance tuning, policy hardening (L3 & L7), Hubble-based observability, multi-cluster networking, and runbook-driven incident response.
Why Cilium, why now
Kubernetes networks are getting busier, stricter, and more app-aware. Cilium’s eBPF dataplane delivers:
- Performance & efficiency: in-kernel packet processing with fewer iptables bottlenecks. (Refer to the image Fig A)
- App-aware security: L3/L4/L7 policies with identity-based enforcement.
- Future-proofing: Gateway API, ClusterMesh, transparent encryption, and rich telemetry via Hubble.
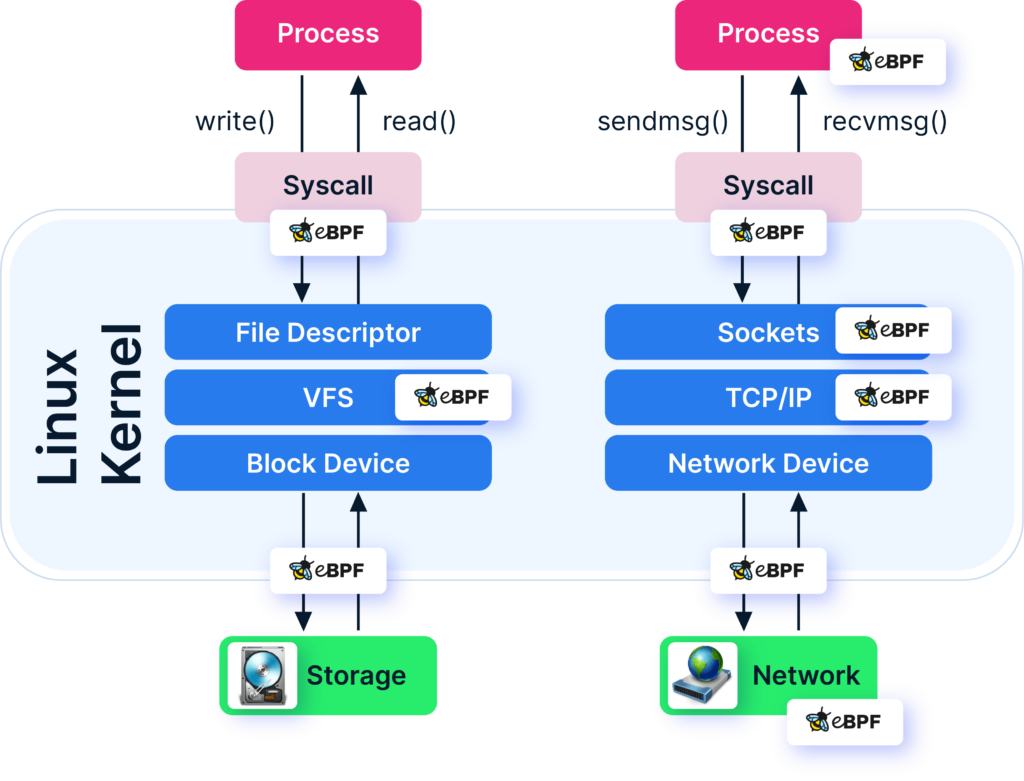
Fig A: Cilium eBPF data plane
A lot of organizations are standardizing on Cilium (a lot of adopters) to squeeze more from infra, reduce p95/p99 latency, and unify networking + security policies across clusters and clouds. We’re here to make that journey safe and fast.
However, there are few experts in Cilium, eBPF, and kernel programming to support Cilium CNI adoption.
(You can argue by saying, “But Cilium CNI is rock-solid stable.”
And I put forth my point: “Well, Cilium is open-source, and if something breaks, how to mitigate those risks in an enterprise?”)
What IMESH offers for Cilium CNI (Day-0 to Day-2)
1) Architecture & Readiness
- CNI mode selection: guidance on chaining vs. isolated modes (Cilium CNI vs AWS CNI), IPAM choices (kube-router, ENI, Azure IPAM, etc.), and node networking prerequisites.
- Design reviews: MTU strategy, kube-proxy-replacement options, encryption choices, BGP vs. native routing, Gateway API fit.
- ClusterMesh planning: multi-cluster/multi-region topologies, service discovery, identity propagation.
2) Secure-by-default Setup
- Install & upgrades: version pinning, helm values hygiene, safe rollback plans.
- Policy program: L3/L4/L7 NetworkPolicy & CiliumNetworkPolicy models, baseline/defense-in-depth, app-owner guardrails.
- Runtime hardening: recommended defaults, limit-blast-radius strategies, zero-trust ingress/egress patterns.
3) Observability & Troubleshooting
- Hubble: real-time visibility into pod and service traffic flows. Debug Cilium CNI issues efficiently with powerful filtering options.
(Refer to the image below Fig B: architect the Hubble to amplify network observability of nodes.)
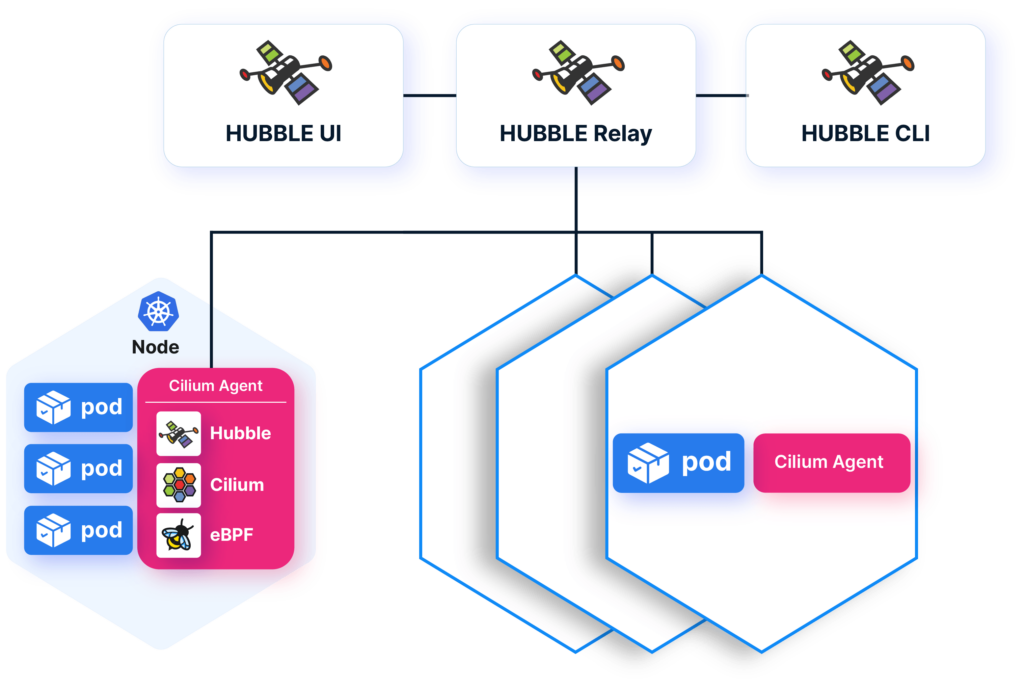
- Proactive health: alerts on dropped packets, policy denials, DNS anomalies, connection track pressure, and identity churn.
- Runbooks: curated playbooks for the top 20 production issues (MTU, routing, kube-proxy-replacement, node-to-node, DNS, etc.).
4) Performance & Cost Optimization
- Latency & throughput: p95/p99 tuning, Smart-NIC readiness, syscall hotspots, ENI/ENI-like limits.
- Node density: CPU/memory profile of Cilium agents, offload options, right-sizing DaemonSets.
- Traffic engineering: load-balancing modes, DSR/Maglev guidance, Gateway API policies.
5) Production Operations(24×7)
- SLA-backed support: enterprise response times, follow-the-sun escalation.
- Lifecycle management of Cilium CNI: CVE & patch advisory, emergency guidance, planned upgrades, safe rollout, and rollback strategies
6) Network Expertise(24×7)
- Network expertise: Expertise in K8s network, including managing and securing east-west and north-south traffic using Istio service mesh and Envoy Gateway.
- Interrelated complexity and dependencies: Impact analysis and dependencies on network functionalities and performance when Cilium CNI is used with Istio service mesh.
Optional add-ons: Training for platform/app teams, tabletop incident drills, and integrations with your SIEM, paging, and ticketing stack.
Migrating from Calico or AWS CNI?
In case you are using AWS CNI or Calico and want to migrate to Cilium CNI, we’ve got a plan:
- Policy translation: map existing NetworkPolicies to Cilium policies (including L7 where valuable).
- Blast-radius control: staged namespaces, progressive enforcement, deny-list dry-runs.
- IP addressing & routing: avoid overlapping CIDRs, plan for IPAM limits, and validate kube-proxy-replacement.
- Success criteria: Define SLOs (latency, error rate, policy hits, drop reasons) before cutover, prove them in the pilot, and carry them into production.
Chaining vs. Isolated: how we help you choose
At times, enterprises may not be ready to fully adopt Cilium CNI, so chaining mode (AWS CNI and Cilium CNI) makes sense.
- Chaining mode: keep parts of your current dataplane while adopting Cilium features progressively—good for brownfield clusters. Read AWS CNI and Cilium CNI.
- Isolated mode: go “all-in” on Cilium dataplane for maximum performance and L7 policy depth—best for greenfield or once you’re confident.
We’ll model the trade-offs against your compliance, team readiness, and migration deadlines.
Cilium CNI enterprise support
If your team requires enterprise support for Cilium CNI, please contact us today.



